The Zerofox Syndicate
Honeypots and Their Purpose
2022-01-12There are two types of honeypots that each have their own purpose and habitat.
The Tripwire
This type of honeypot lives on the internal corporate network and is mainly used for detecting network intrusions. Ideally located among other important servers that an intruder might take an interest in. This honeypot wants to maximize the chances that an attacker on the local network interacts with it.
When an attacker interacts with the honeypot, for example by scanning it or trying to sign-in on it, an alert is generated and sent to a system administrator to investigate. This is how network intrusions can be detected.
The Insect Trap
Another type of honeypot mainly lives on the public internet. This one tries to trap malware payloads and observe attacker behaviour. It logs the attacks and helps security researchers understand how new types of attacks work.
They are a useful source of malware samples for malware researchers. Malware researchers investigate samples those to improve anti-virus software and develop other measures against new malware.
The two types of honeypots differ in how they are designed and what their purpose is.
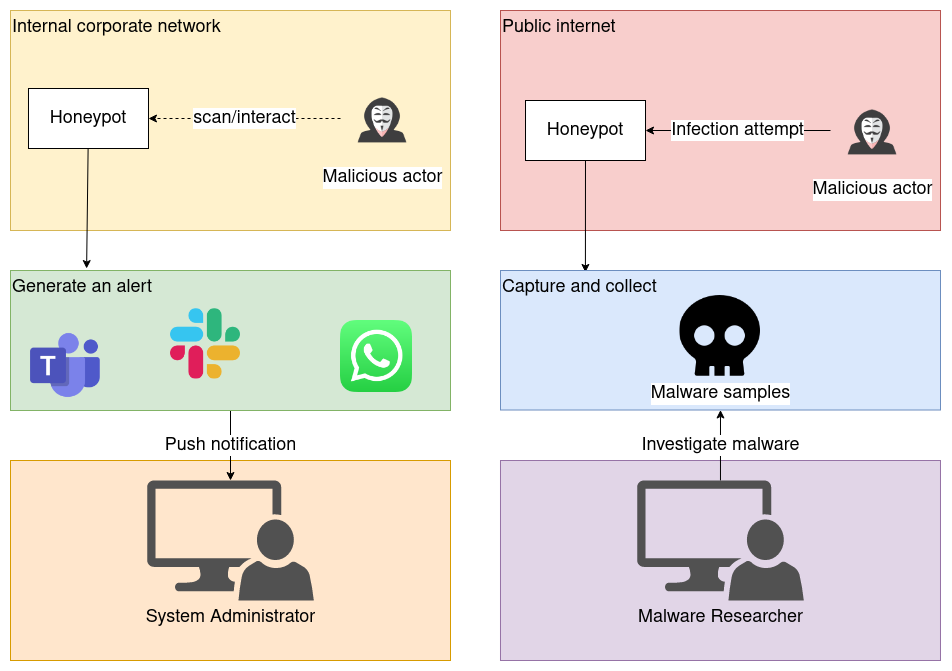
Setting up a honeypot that is designed to log and capture malware on your local network is unlikely to be very useful. Equally, setting up a public honeypot that sends you an alert messages everytime some unknown party interacts with it is likely annoy you, without providing any value.
two log4shell honeypots
The log4shell vulnerability (CVE-2021-44832) is very popular among attackers right now. I recently came across two honeypots that both focus on detecting potential attacks that abuse this vulnerability.
BinaryDefense made a Python honeypot to detect someone scanning or trying to exploit this vulernability on your local network. When an attempt is detected this honeypot will call a webhook. This allows you to create push notifications, for example to a MS Teams channel.
MalwareTech also made a honeypot in Python to log Log4j attacks. The purpose of this honeypot is to figure out how malware works and allow the owner to study it. MalwareTech has a Youtube video where he explains and demonstrates the use of his honeypot.
Technologically, both of these honeypots are similar. They are both written in
Python and try to detect ${ characters in web requests but they differ
significantly in what they do with this information.